Share Article
How to sign files with Azure Sign Tool
Azure Sign Tool is a open source command line tool which can be used to digitally sign files using codesign certificates stored in Azure Key Vault. The usage is similar to Microsoft Sign Tool and can be used with many of the same commands. The tool can be used to sign with both standard and EV codesign certificates stored in Azure Key Vault.
Azure Sign Tool is a open source command line tool which can be used to digitally sign files using codesign certificates stored in Azure Key Vault. The usage is similar to Microsoft Sign Tool and can be used with many of the same commands. The tool can be used to sign with both standard and EV codesign certificates stored in Azure Key Vault.
Note: The tool is not developed by Microsoft, but by independent developer Kevin Jones.
Prerequisites
- Azure Key Vault
- Standard or EV codesign certificate stored in Azure Key Vault
(Please see the following link for a guide on this subject: How to Set Up, Install, and Use an EV Code Signing Certificate (Azure)💡 (trustzone.com)
Installing Azure Sign Tool
If you wish to build the tool from source or take a look at the sourcecode the github repository which can be found on this link: vcsjones/AzureSignTool: SignTool Library and Azure Key Vault Support (github.com)
The tool can also be installed with the dotnet command which is part of the .NET SDK.
The .NET SDK can be downloaded from this link Download .NET (Linux, macOS, and Windows) (microsoft.com)
When the SDK has been installed the following command can be used to install the tool:
dotnet tool install --global AzureSignTool
The tool can then be used in a PowerShell prompt by using the command:
azuresigntoolRegistering Azure Sign Tool as a Azure Application
To ensure that Azure Sign Tool can connect to your Azure Key Vault it has to be registered as an application in Azure. Then the credentials needed for the tool to authenticate has to be generated and the correct access needs to be set on the Key Vault.
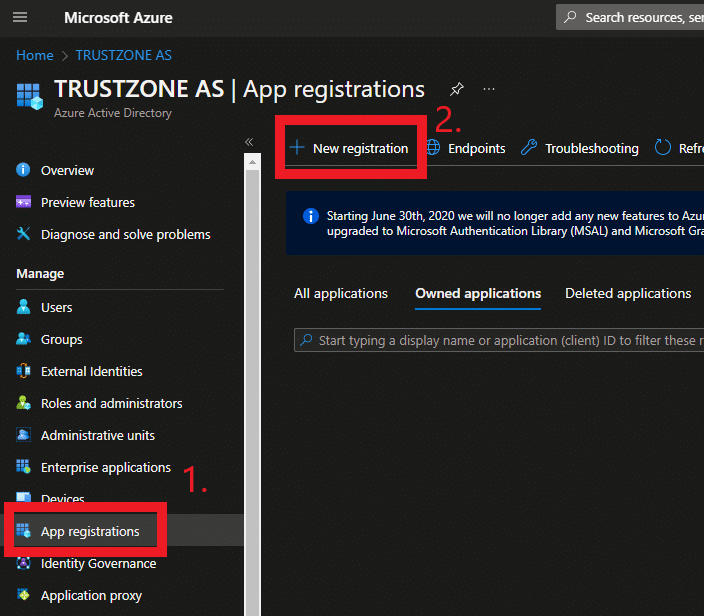
- Log into your Azure portal and navigate to Azure Active Directory
- Click on App Registrations in the action bar to the left
- Click on New registration
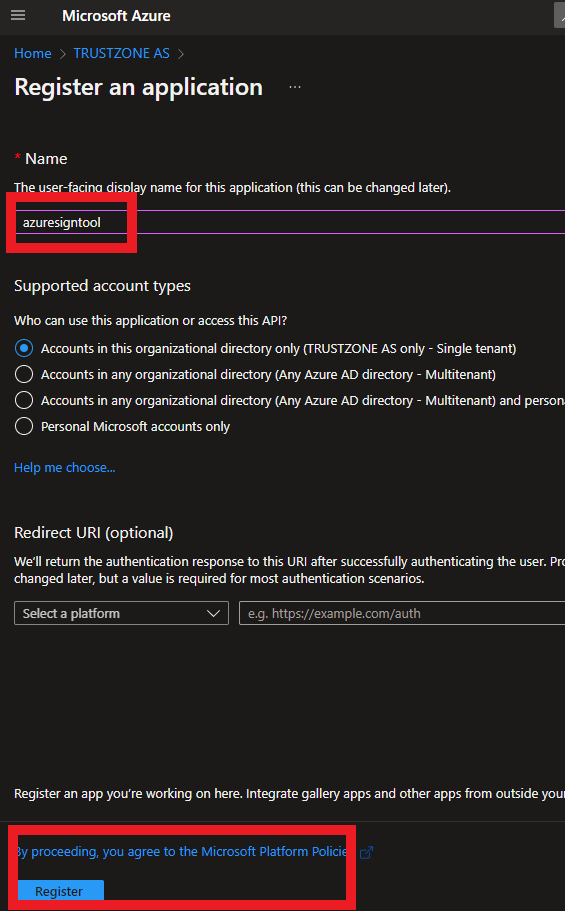
- Name the application and click Register (fx. azuresigntool)
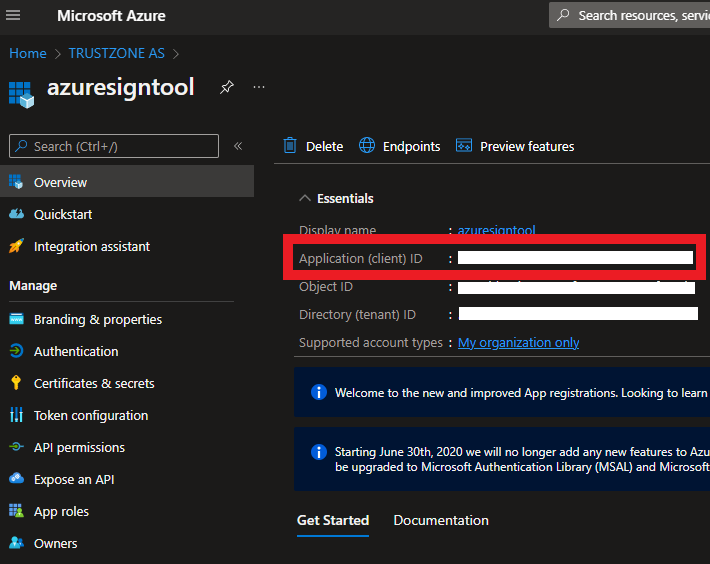
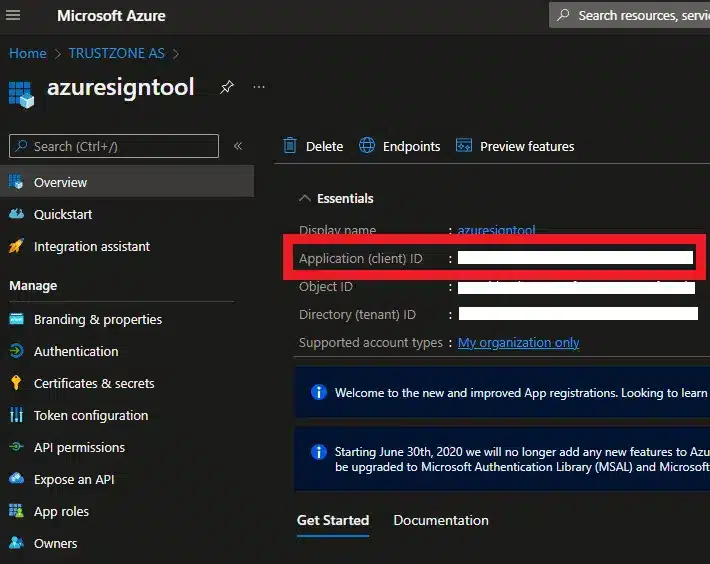
- Copy the Application (client) ID
- Select Certificates & secrets in the action bar to the left
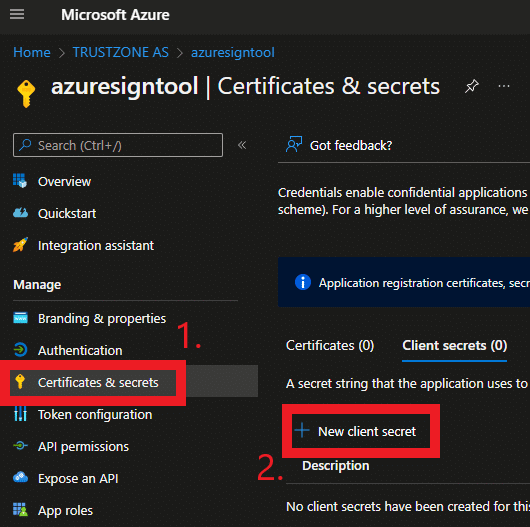
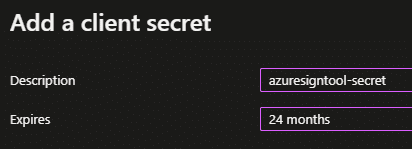
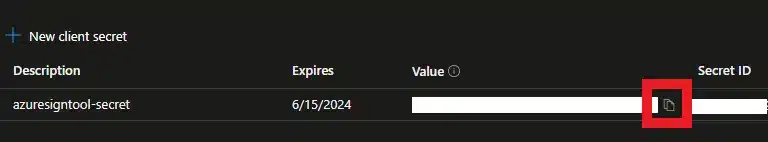
- Click “+ New client secret”. Then add a description and select an expiration for the secret. When the secret expires a new one has to be generated to use the Azure Sign Tool.
- Copy the value field of the secret to a secure location
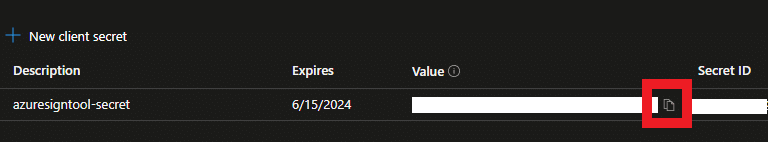
Note: You will be unable to access the client secret when you navigate away from the site, so make sure to copy it.
Configure Access Policy in Azure Policy
After the application has been configured. An Access Policy needs to be configured in the Azure Key Vault where the codesign certificate is stored, so that the application can access the certificate
- Navigate to the Azure Key Vault where your certificate is located.
- Select Access policies in the action to the left
- Then click “+ Add Access Policy”
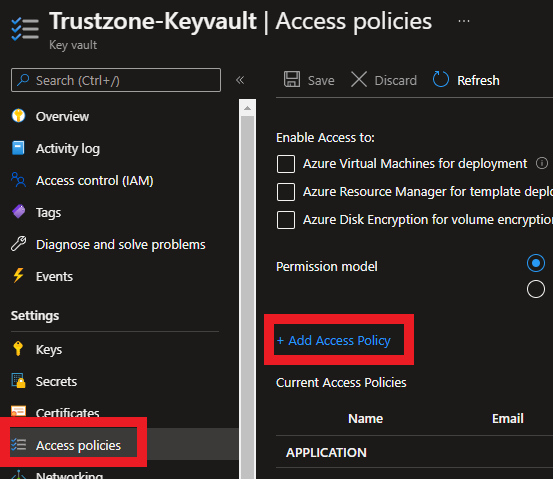
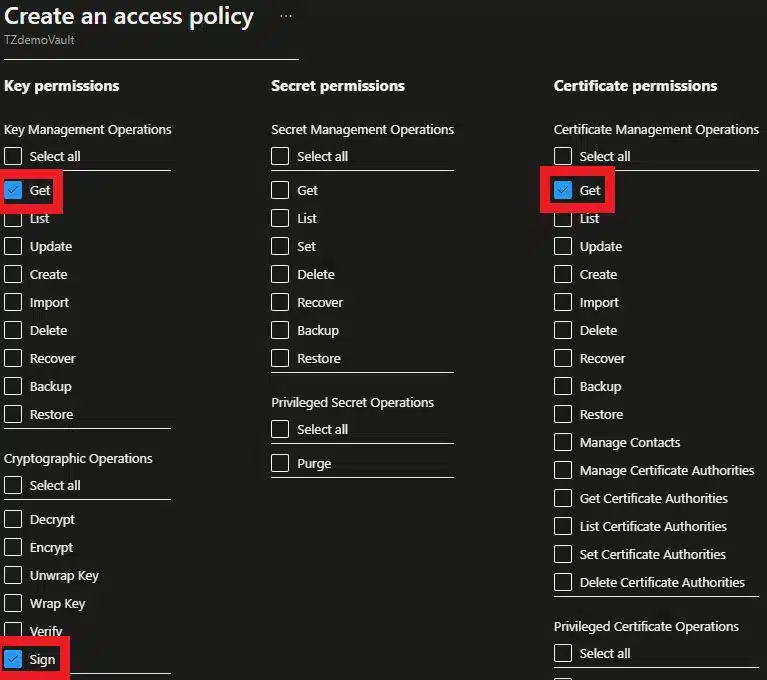
- Set Key Management Operations to “Get”, Certificate Management Operations to “Get” and Cryptographic Operations to “Sign” on you new access policy
- Then click Next, then search and select the correct principal that was made earlier in the guide (the application registered)
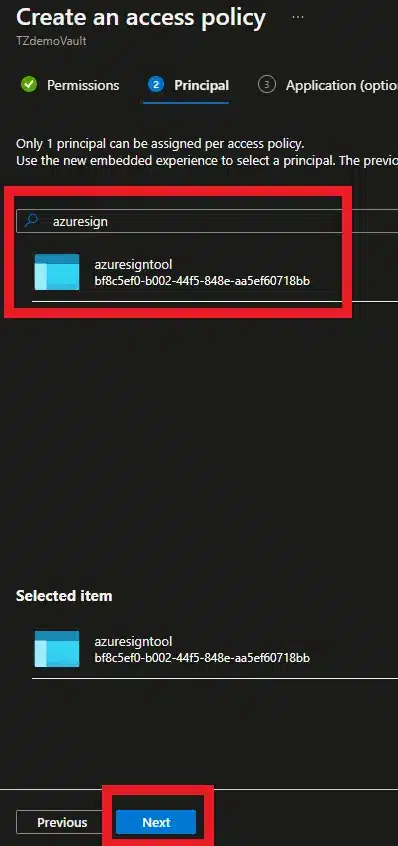
- Click Next until you get to the “Review + create” section. Then click Create.
Signing with Azure Sign Tool
When the application has been registered and the access policy configured you can start signing your files.
To sign you will need the following information:
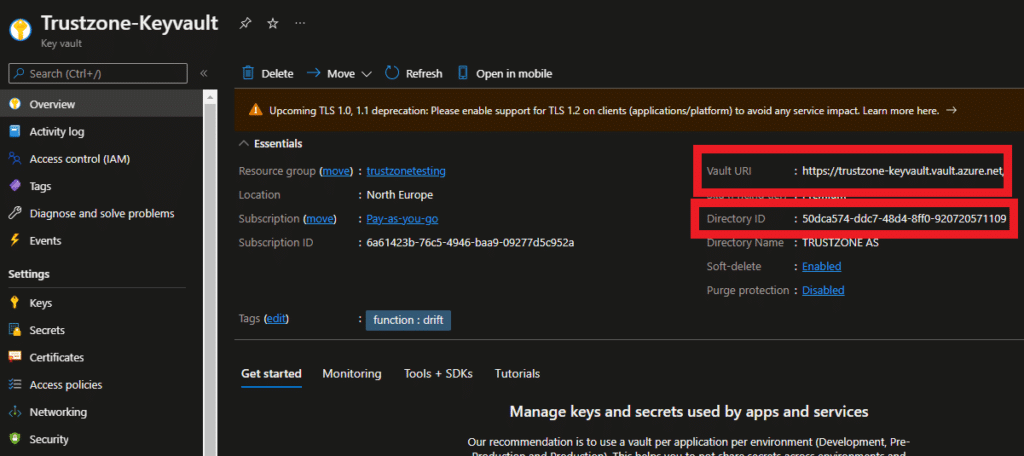
- Key Vault URI
- Directory ID
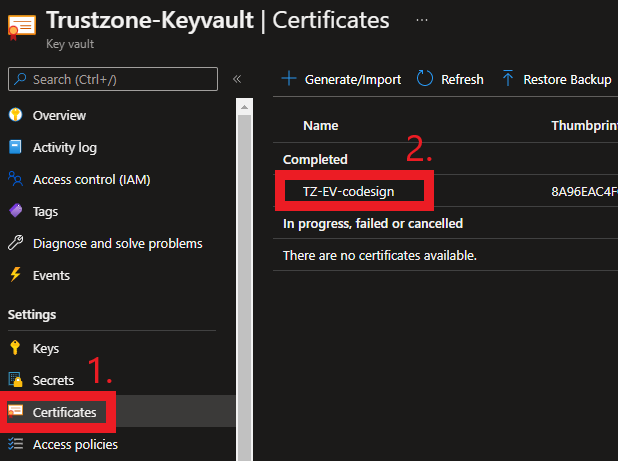
- Friendly Name of your codesign certificate
- Application (client) ID from the Azure Application set up earlier
- Client secret, which you (hopefully) copied to a secure location
With these five pieces of information you can now use Azure Sign Tool on your local device to sign your files using the following command:
azuresigntool sign -kvu Key_Vault_URI -kvt Directory_ID -kvc Friendly_Name -kvi Application_ID -kvs Client_Secret -tr http://timestamp.globalsign.com/tsa/r6advanced1 -td sha256 file_to_be_signed
