Share Article
What you need to know about TLS 1.3
SSL/TLS certificates are essential to any website, online service, or blog. They are used to encrypt communication between servers and clients, ensuring that no one can eavesdrop on or tamper with data being exchanged.
24 July 2022 | 10 mins read | By Jon Drejer Tittmann
What you need to know about TLS 1.3
July 24, 2022
5 min read
The first version of the TLS protocol was released in 1999. Three major revisions have been made since then. The latest version, TLS 1.3, was released in August 2018, but its use is still quite limited.
How TLS works
TLS (Transport Layer Security) is an encryption protocol for securing data that is sent between a client and a server over the Internet. It is the most familiar to users when browsing websites, where the padlock icon appears as part of a secure session that has been established through an SSL certificate. However, TLS does not secure data on end systems. It simply ensures the safe delivery of data over the Internet, thereby avoiding any possible eavesdropping and/or alteration of the content exchanged between applications.
What are the advantages of TLS 1.3 over previous versions?
TLS 1.3 offers several improvements, notably a faster handshake and a simpler and more secure set of cipher suites. By also supporting zero-round-trip-time (0-RTT) key exchanges, TLS handshakes are further streamlined. As a result, performance and security are enhanced.
The faster handshake
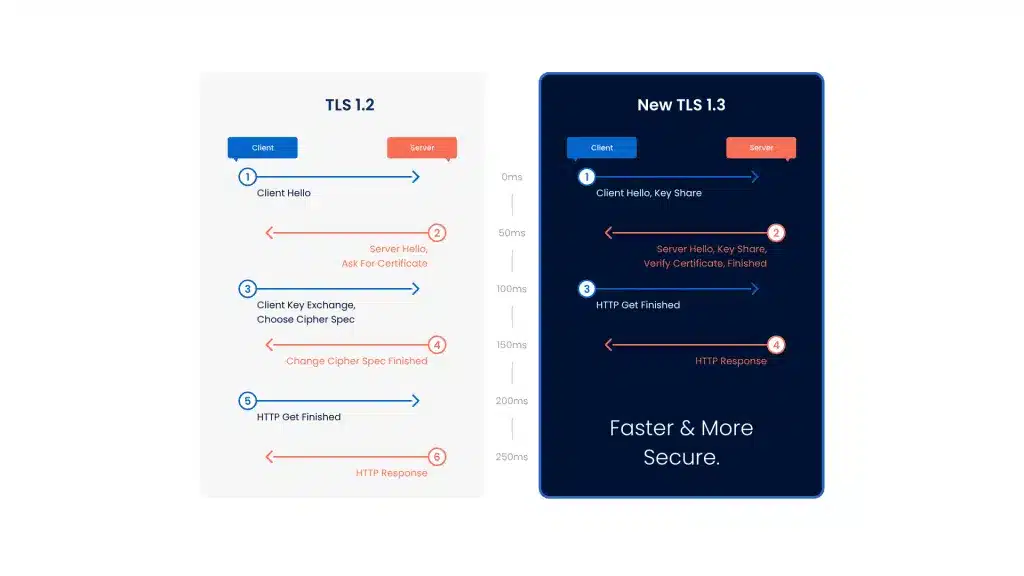
TLS somewhat degrades secure network communication because it requires CPU time and adds latency. Under TLS 1.2, the initial handshake is carried out in clear text, meaning it has to be encrypted and decrypted. A typical handshake involves 5-7 packets exchanged between the client and the server, which adds considerable overhead to the connection. With version 1.3, server certificate encryption is adopted by default. With this change, a TLS handshake can be accomplished with 0-3 packets, as illustrated below, reducing or eliminating this overhead, and enabling faster and more responsive connections.

Improved security through stronger Cipher Suites
The problem with TLS 1.2 is that it is often not appropriately configured, which leaves websites vulnerable to multiple attacks, e.g. POODLE, Heartbleed, or The ROBOT attack. TLS 1.3 removes the obsolete and insecure cryptographic features from TLS 1.2 and only supports Ciphers and Algorithms with no known vulnerabilities, including any that do not support Perfect Forward Secrecy (PFS). In addition, TLS 1.3 removes the ability for the client and server to “renegotiate” that would have allowed clients and servers to generate new keys and parameters during their already established TLS connection, which is a function that would have increased risk.
The good and the bad of Zero Round Trip Time (0-RTT)
In short, Zero Round Trip Time Resumption or 0-RTT optimizes the performance for clients who are revisiting your site. However, the improvement comes at a cost. More precisely, it is a security concern when it comes to 0-RTT, which does not provide a guarantee of non-replay between connections. If an attacker somehow manages to get hold of your 0-RTT encrypted data, it can fool the server into believing that the request came from the server since it cannot know where the data initially came from. If an attacker sends this request multiple times, you could be vulnerable to “a replay attack”.
Is it time to upgrade your web applications to TLS 1.3?
The decision to upgrade to TLS 1.3 at this point will depend on your requirements and motivations. Some browsers do not support TLS version 1.3, which could result in a bad user experience. However, if you disable vulnerable features like renegotiation and use Perfect Forward Secrecy (PFS), TLS 1.2 will have the same security and privacy benefits as TLS 1.3.
There is no doubt that TLS 1.3 is the future of cryptographic protocols, but TLS 1.2 will continue to exist for quite some time. If you want to inspect your domains for supported TLS-versions and any possible vulnerabilities, check out SSL360®.
Submit Your Technical Queries Here for Expert Assistance!
We will contact you as soon as possible.
Please enter your details below.

